Protecting Owncloud Against Bruteforce Attacks With Fail2ban
Requirements:
- OwnCloud 7.0.2 or higher installed
- Fail2Ban installed
1- Configuring Fail2Ban
Copy Fail2Ban configuration file, never use jail.conf, it will get overwritten when fail2ban is updated.
cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
2- Open the configuration file:
vi /etc/fail2ban/jail.local
Append at the end of the file:
#OwnCloud
[owncloud]
enabled = true
filter = owncloud
action = iptables-multiport[name=owncloud, port=”http,https”]
logpath = /home/yourusername/public_html/data/owncloud.log
maxretry = 5
enabled: Should be set to true for fail2ban to ban the offending IPs.
filter: the filter filename, which will be created in the next step.
action: the action that will be taken when the maximum number of failed logins is reached. In this example, we’re blocking both the http and https port (port 80 and 443 by default).
logpath: the path to owncloud log file. As of ownCloud 7.0.2, the log file is automatically created in the data directory. If you’re using an older version of ownCloud that doesn’t create a logfile, you can create log file and add it to the logpath. For example:
vi /var/log/owncloud.log
chown oc:oc owncloud.log
maxretry: the allowed number of failed login attempts before fail2ban bans the IP.
3- Create a filter for ownCloud and add the following inside it:
For Owncloud 7
vi /etc/fail2ban/filter.d/owncloud.conf
[Definition]
failregex={“app”:”core”,”message”:”Login failed: ‘.*’ (Remote IP: ‘<HOST>’, X-Forwarded-For: ‘.*’)”,”level”:2,”time”:”.*”}
ignoreregex =
For Owncloud 8
vi /etc/fail2ban/filter.d/owncloud.conf
[Definition]
failregex={“reqId”:”.*”,”remoteAddr”:”.*”,”app”:”core”,”message”:”Login failed: ‘.*’ (Remote IP: ‘<HOST>’, X-Forwarded-For: ‘.*’)”,”level”:2,”time”:”.*”}
ignoreregex =
4- Setting ownCloud log file
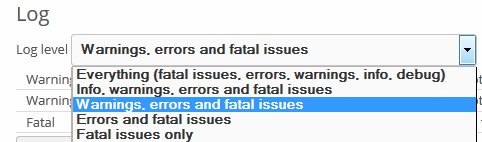
Go to ownCloud, click on your username on top right, go to Admin section, scroll down to the Log section and choose: warnings, errors and fatal issues.
5- Restart fail2ban
service fail2ban restart
Fail2ban should now ban all the IPs that are failing the login 5 times.
Have Any Questions? Please let me know!